Form submissions and lead collection are important aspects to consider when hosting websites. If you have ever managed a website that has an open form on it, you know spam is inevitable. Most of the sites built on Zesty.io are geared for marketing, so every lead counts. Because of this, adding a captcha isn’t always the best idea because it can kill conversions. There's another way to be clever when it comes to skirting bot submission: honeypot.
Implementing a Honeypot
What is a Honeypot?
“In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site, but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, who are then blocked. This is similar to police sting operations, colloquially known as "baiting," a suspect.” (Source)
When adding a honeypot, we're setting a trap that a bot doesn’t know about. In our case, it will be a hidden input field on a form. We will turn this into a honeypot by making it look like a field that should have a value and reject the form submission if it does. This should help with fooling many form submission bots that programmatically submit forms with all of the fields set to values. As there is no way for the bot to know which of the fields is the honeypot (that information remains on the server), it should be fooled into providing a value, which causes the submission to fail.
The Zesty.io platform supports the use of a honeypot field for forms rendered by the web engine component. This has been implemented by allowing the form designer to specify the name of a field to be used not for real data from the front end, but as a trap for bots. Let’s assume for the sake of example that we have set our honeypot field name to be “workemailaddress”. Once this setting has been configured in Zesty.io's manager interface, the Zesty.io web engine will behave as follows when processing form submissions:
- If the form does not have a field named “
workemailaddress” (the honeypot field), the submission will be rejected with a 500 error. - If the form has a field named “
workemailaddress” and that field contains a value then the submission will be rejected with a 500 error. - If the form has a field named “
workemailaddress” with no value set then the submission will succeed.
Adding the honeypot field to the forms in your view templates is as simple as adding any other form field:
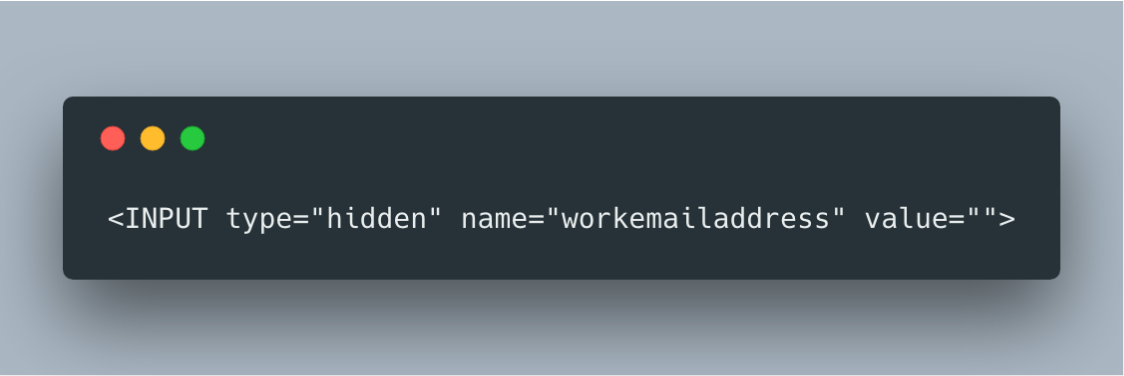
If this remains unchanged during form submission then the form will post successfully. If a value is added then the server will reject the form submission with a 500 error. Regular users won’t see this form field as it is of type “hidden” and will not be rendered by the browser.
Why Use a Honeypot over Captcha
Implementing a honeypot is one way that you can help improve the quality of form submissions that you receive from your website. With Zesty.io, this feature is extremely easy to add and requires no coding as the platform handles it for you. In other platforms, it may require more development resources.
If you're interested in learning more about this and other security features built into Zesty.io, please reach out.